Blueprints
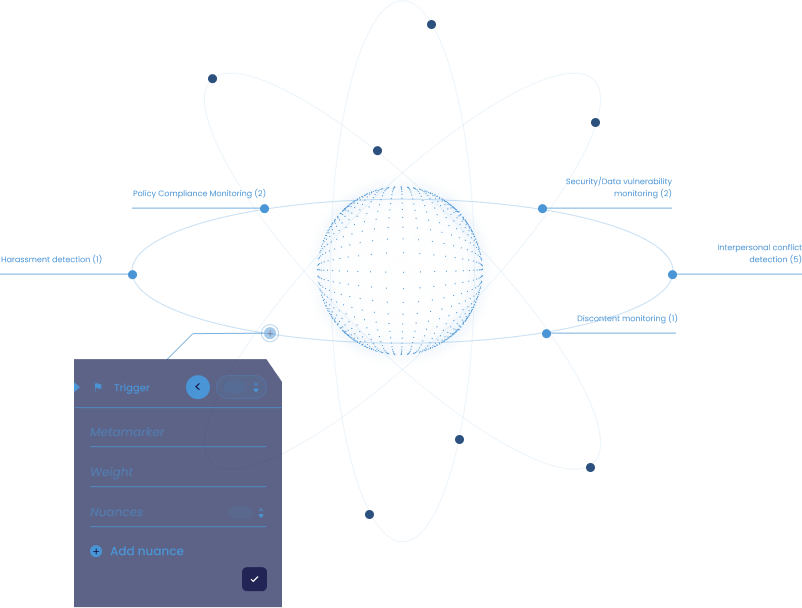
Define and customize your organization's policies and protocols with Blueprints. Set nuanced rules, thresholds, and guidelines to align interactions with your unique requirements.
Protocols
Specify the number of protocols or rules within each Blueprint to ensure comprehensive coverage of your compliance and ethical standards.
10
Templates
Access pre-built Blueprints for common compliance areas, or use them as a starting point to create customized Protocols tailored to your Organization.
4
Collaborate
Manage multiple Blueprints to address different areas of your organization and different priority timeframes.
1
Test mode
Test and simulate your Blueprints in a safe environment before deploying them globally, ensuring accuracy and identifying potential issues.
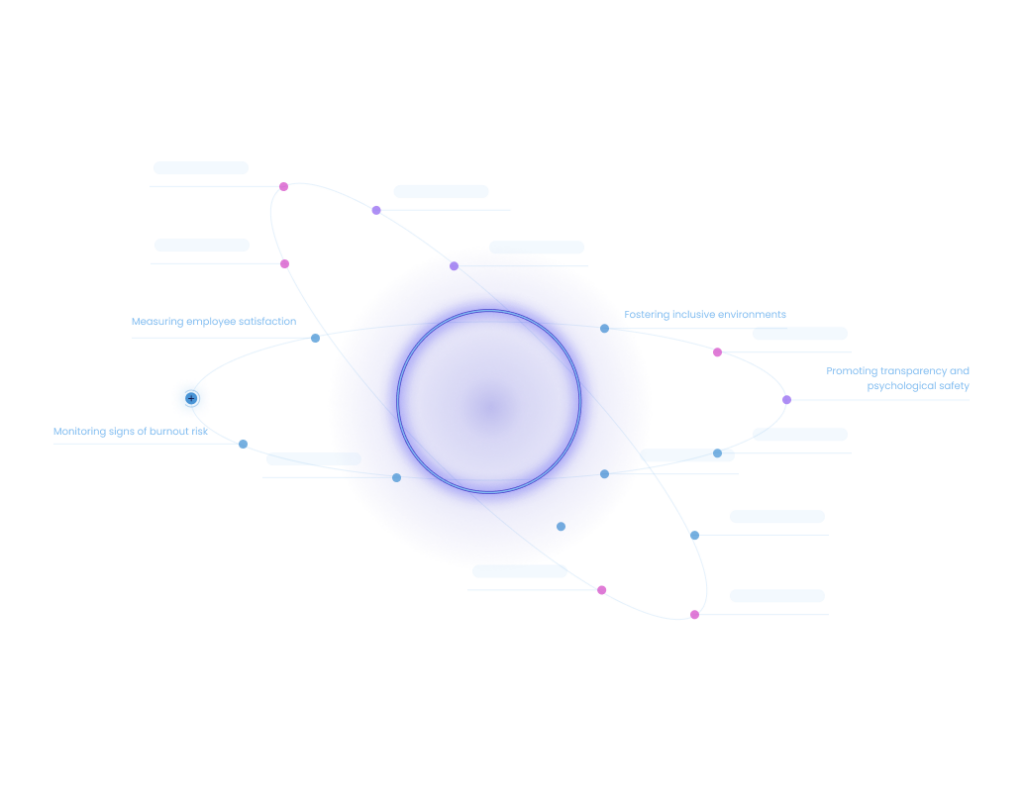
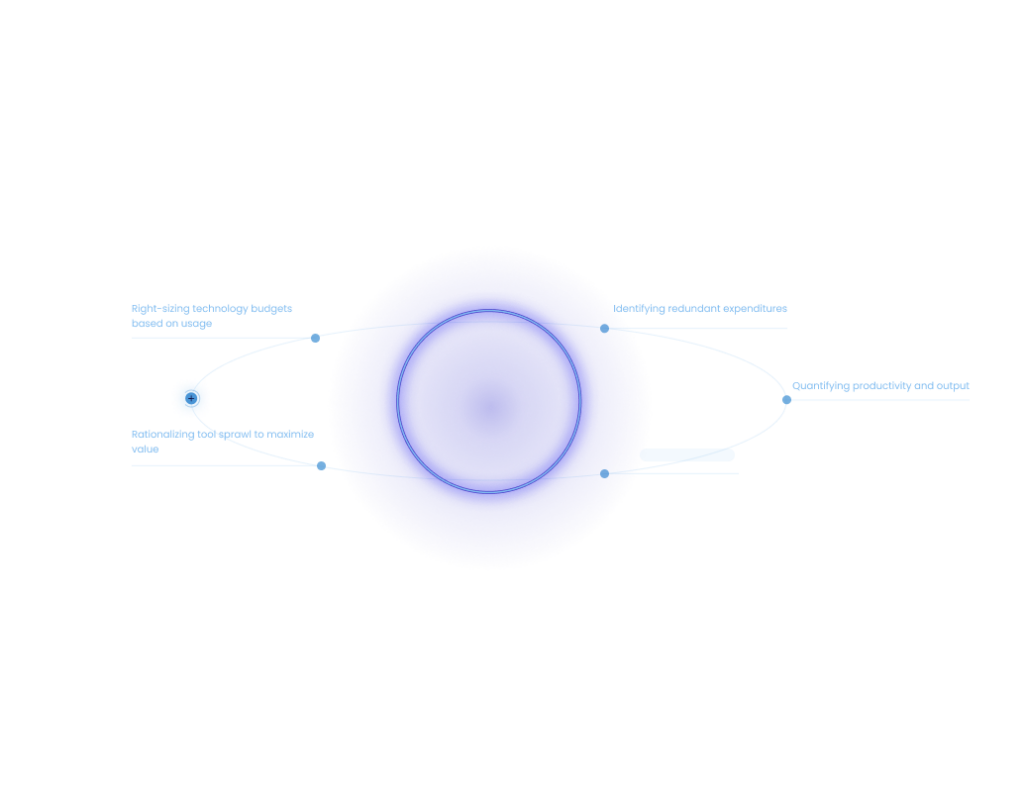
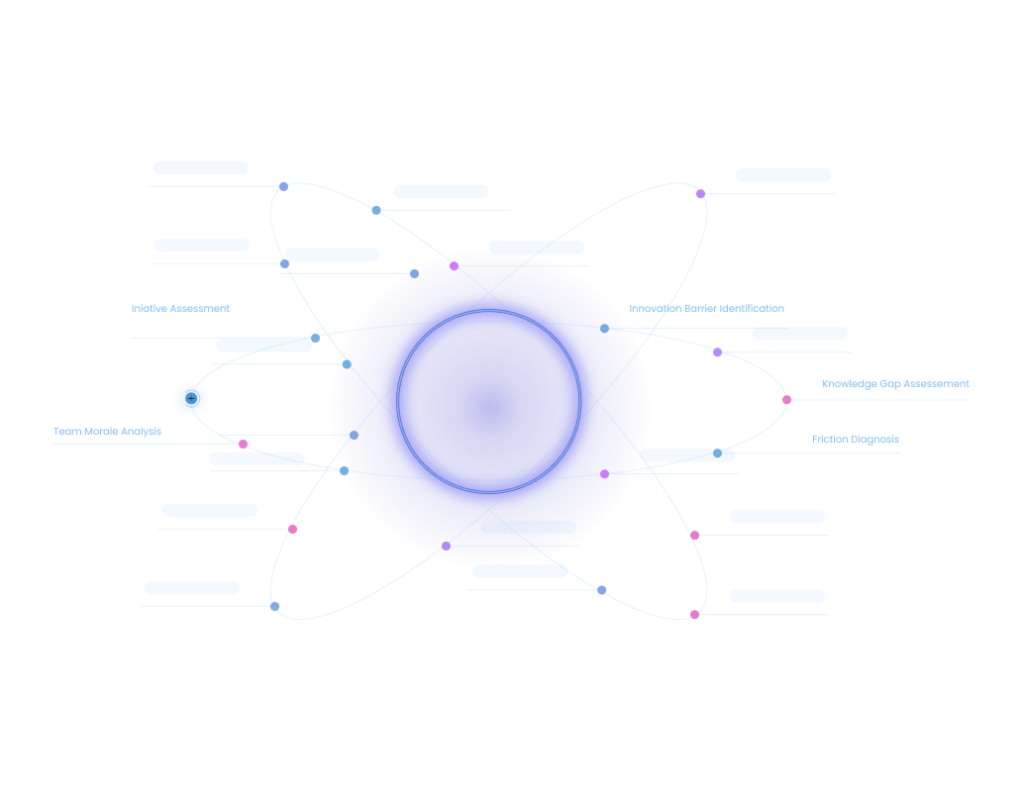
Interaction Patterns
Protocols are based on a set of categories to cover the key aspects of a liability management - defensible Policies, proactive decision guidance, best practice promotion, performance tracking, and continuous learning/improvement.
Custom Policies Access
Policy is a foundational protocol type capturing your organizational policies, regulations and compliance mandates that must be adhered to in order to mitigate liabilities.
500 users
Analytics
Gain valuable insights into potential flags, breaches, risk areas, and anonymised employee interactions through comprehensive analytics and reporting.
Quick View Upcoming
A set of individual statistics that provide a quick overview of your members' engagement, interactions and interest levels across different areas of the application.
Engagement
Monitor and analyse employee engagement levels with your organization's policies and compliance initiatives.
Trends
Visualise Log trends over time.
Flags
Receive real-time notifications or "flags" when EVA detects potential issues or deviations from your defined policies, enabling proactive intervention.
Users Roles
Global Admin
GAs Have full permissions to manage all features including creating, editing, archiving, publishing, deleting Blueprints, managing billing, accessing the Library, accessing analytics, and managing members across all roles.
Member
Has a view-only role for Published Blueprint with potential to add comments or feedback, stay aware of guidelines and can view the Organisation's members list.